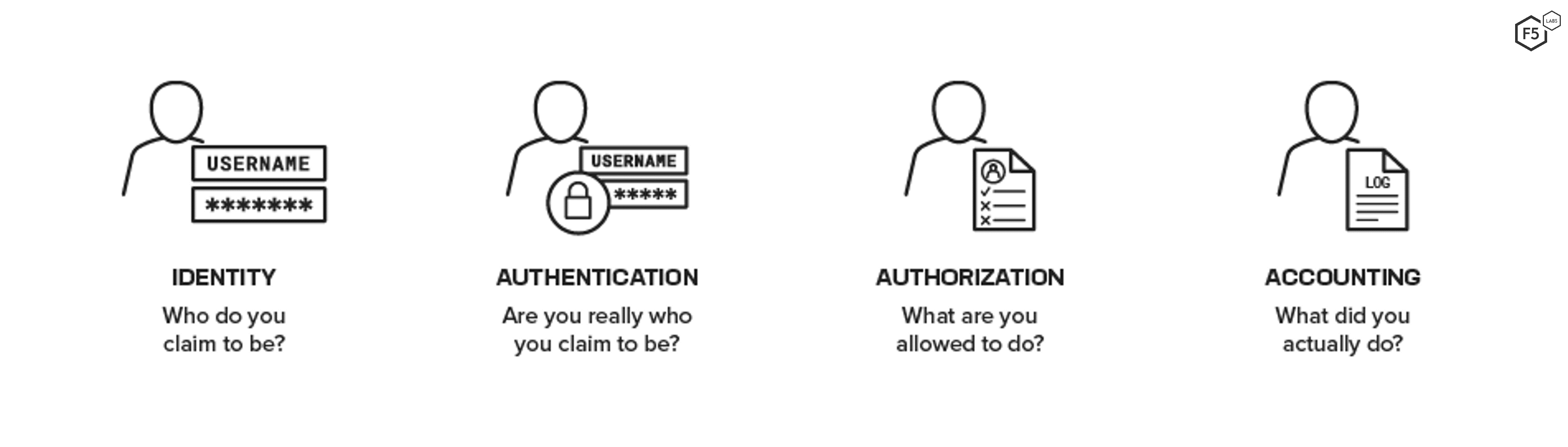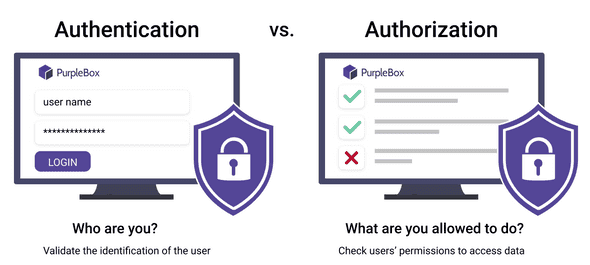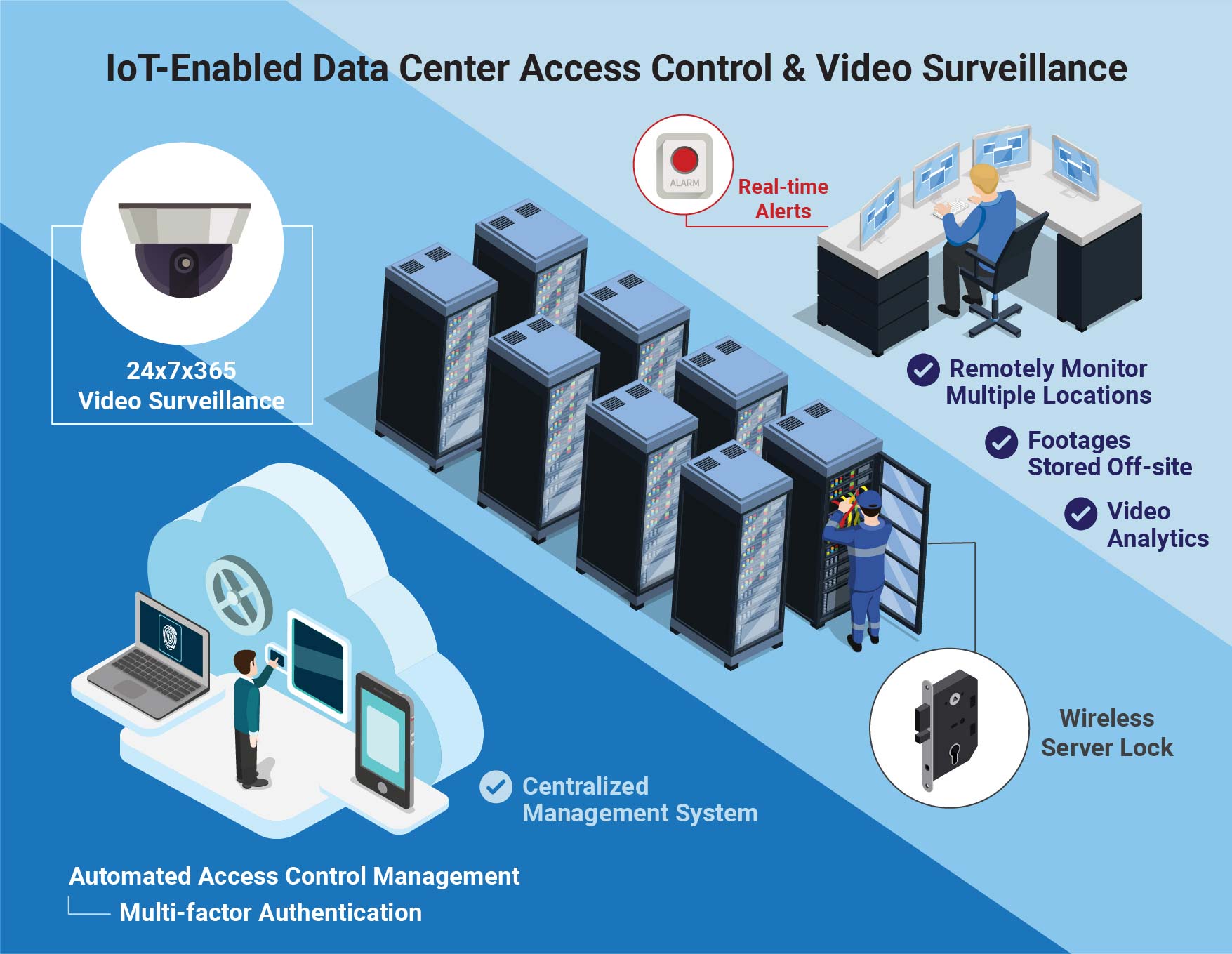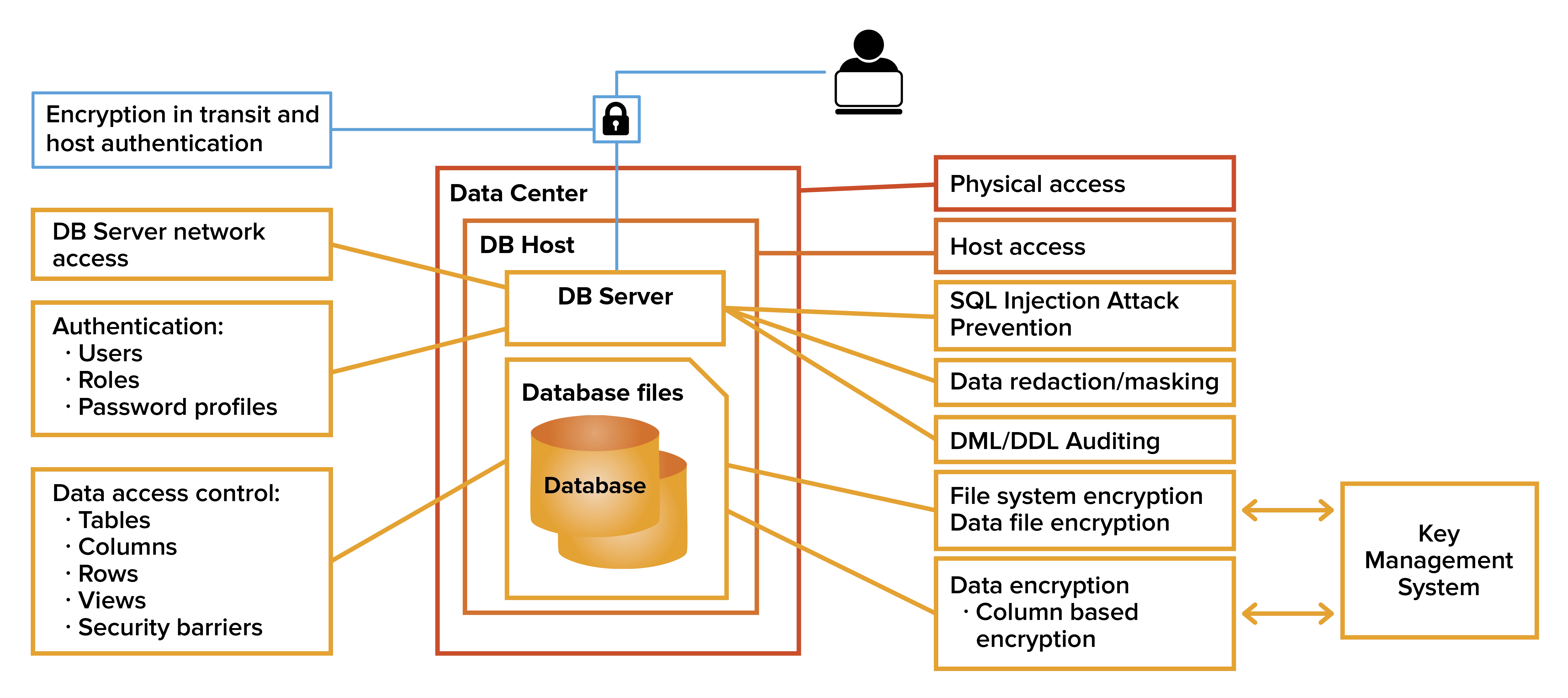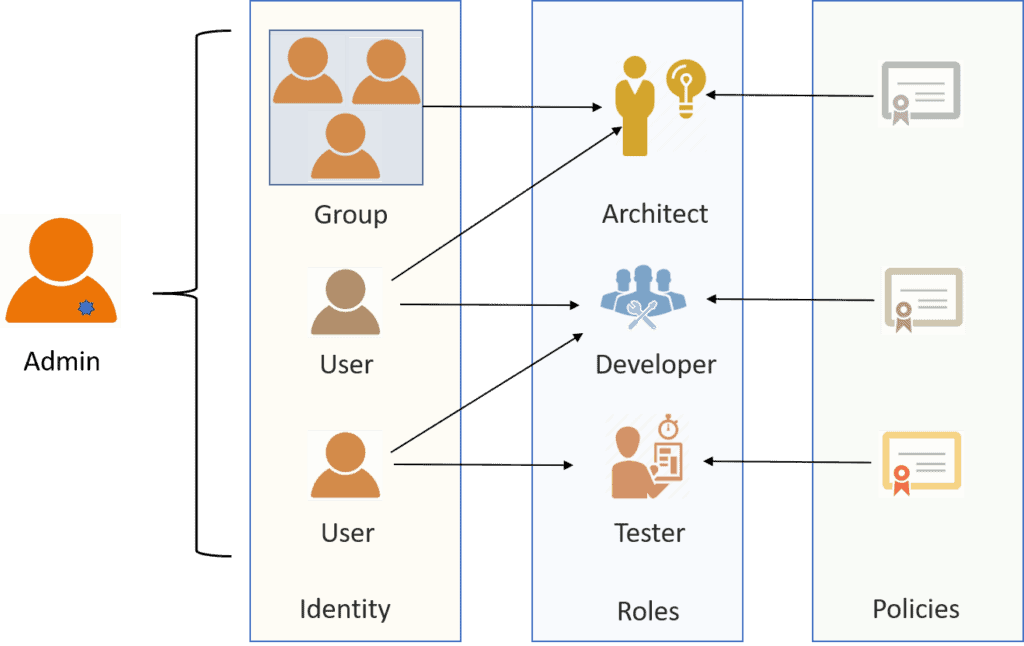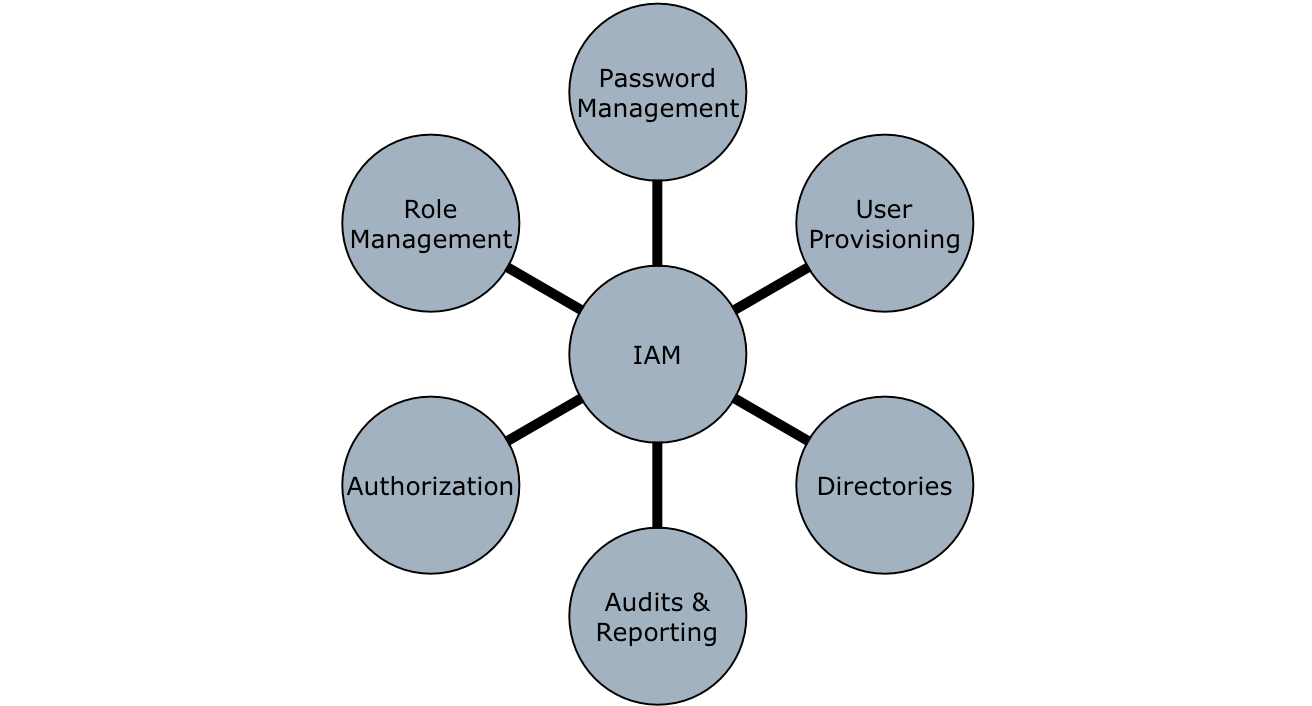
3 Basic A's of Identity and Access Management -Authentication, Authorization, and Accounting – Xorlogics

Free Course: Information Security - Authentication and Access Control from New York University (NYU) | Class Central

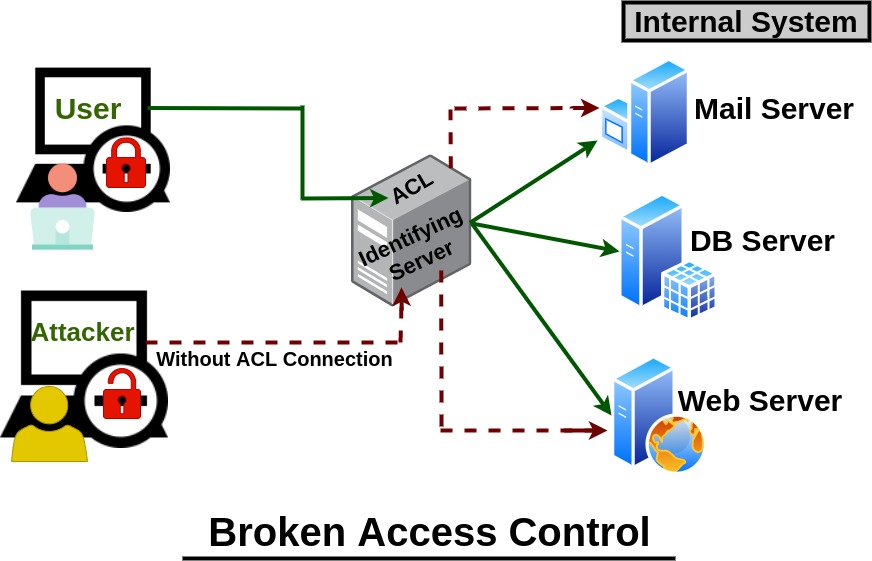
Authentication vs. Access Controls vs. Authorization | by CloudKnox Security Inc. | CloudKnox Security Inc. | Medium
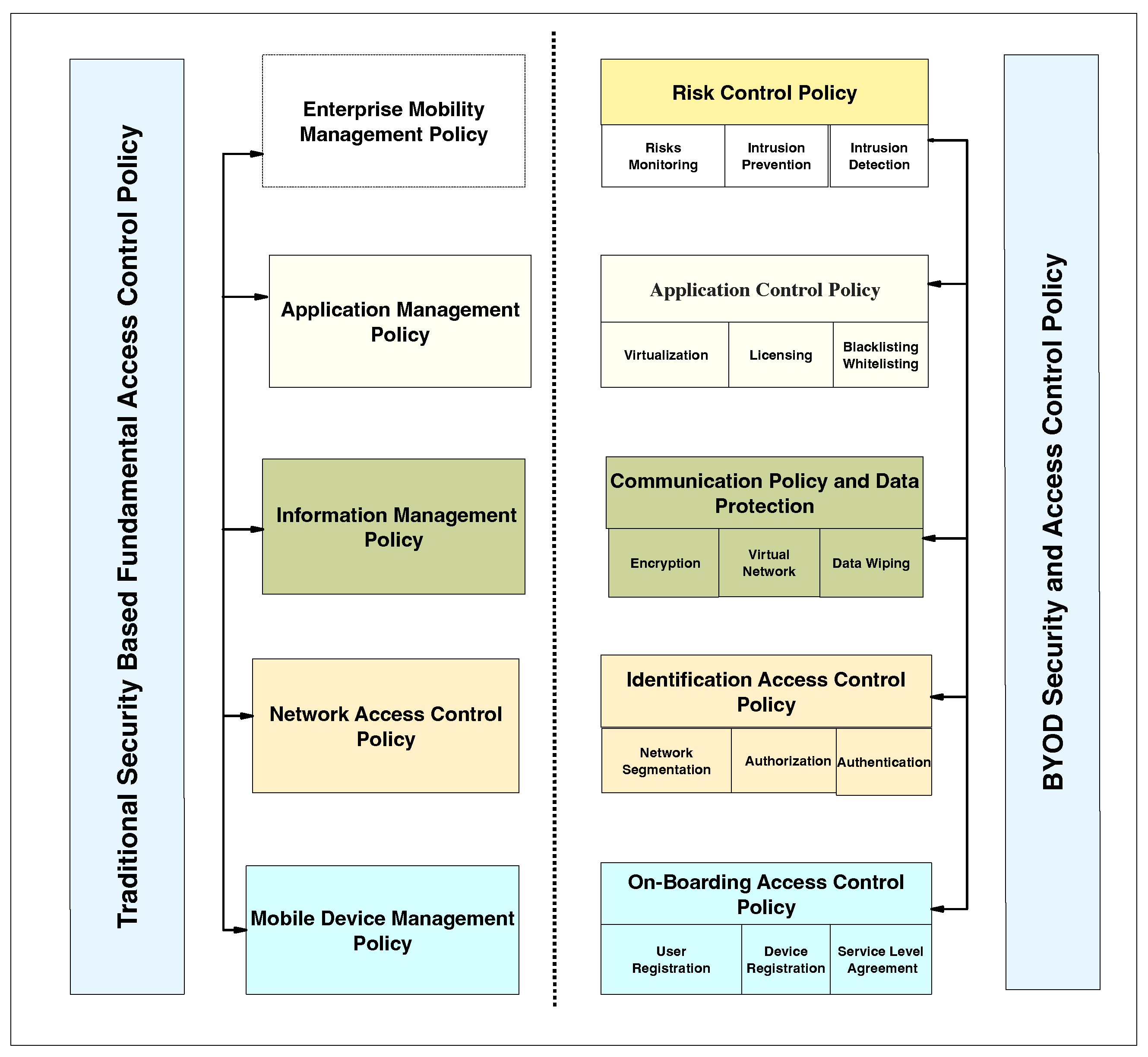
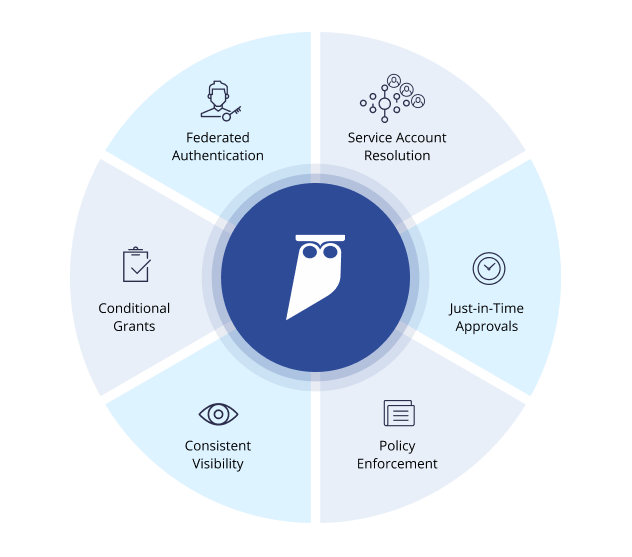
Applied Sciences | Free Full-Text | Systematic Literature Review on Security Access Control Policies and Techniques Based on Privacy Requirements in a BYOD Environment: State of the Art and Future Directions