![PDF] Analysis of Common Access Control Models and Their Limitations in Cloud Computing Environment | Semantic Scholar PDF] Analysis of Common Access Control Models and Their Limitations in Cloud Computing Environment | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/274d2313b4c103a022a5a974716a00a6dc2d3000/3-Table1-1.png)
PDF] Analysis of Common Access Control Models and Their Limitations in Cloud Computing Environment | Semantic Scholar

Access Control Models and Methods - Types of Access Control | PDF | Computer Access Control | Cyberspace

Rationale for the RBAC96 family of access control models | Proceedings of the first ACM Workshop on Role-based access control

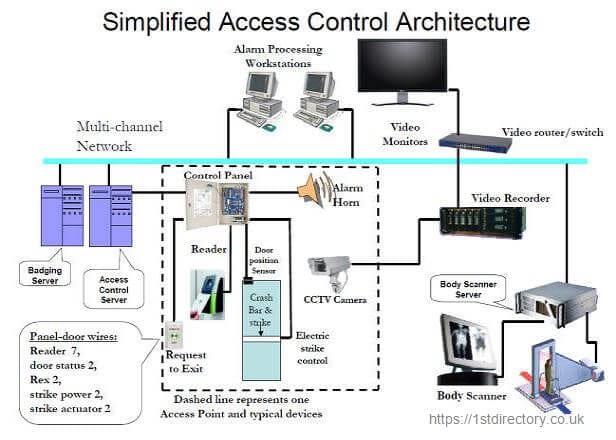


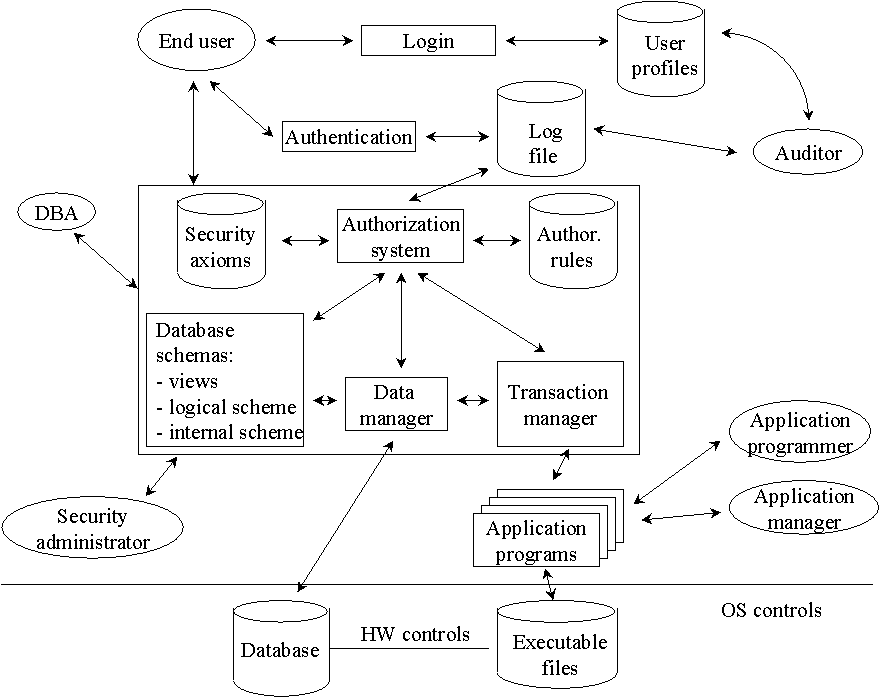

![PDF] Methods for Access Control : Advances and Limitations | Semantic Scholar PDF] Methods for Access Control : Advances and Limitations | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6192f0308dc8d7782b55a0557dfb66f323638853/4-Figure1-1.png)


![PDF] Review the Types of Access Control Models for Cloud Computing Environment | Semantic Scholar PDF] Review the Types of Access Control Models for Cloud Computing Environment | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4dd58d7ef7f99a18255704c0733da18c49154787/4-Table1-1.png)


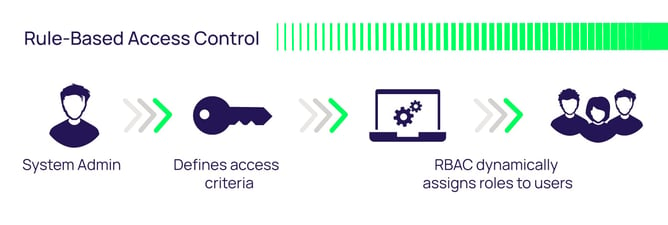
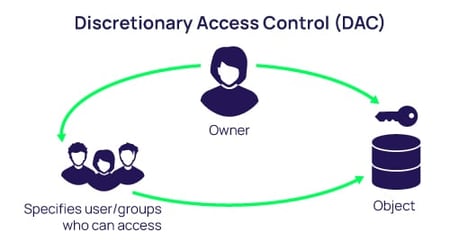
![The 4 Types of Access Control Models Explained [+Examples] The 4 Types of Access Control Models Explained [+Examples]](https://butterflymx.com/wp-content/uploads/2023/01/Access_control_models_tips-jpg.webp)